Abstract Link to heading
Windows prefetch files are temporary files stored in the %SystemRoot%\System\Prefetch folder. This memory management feature is keeping track of the frequently running applications on a given system. We can extract some data from those files in order to get useful information for a digital forensic investigation. In this blog article, I will explain how we can use memory forensic to extract prefetch files, parse them and create in the end a volatility3 plugin.
Windows Prefetch file format Link to heading
Windows prefetch files are constructed with one file header and multiple sections. In each sections different information can be found in which there can be some interesting valuable forensic artifacts. With the evolution of the Windows versions, prefetch files format changed we will see later those changes and the differences between them. Integers are stored in little-endian order, Strings in UTF-16 little-endian and Timestamp in Windows FILETIME UTC. You can see bellow a representation of a prefetch file header and how the information is stored:
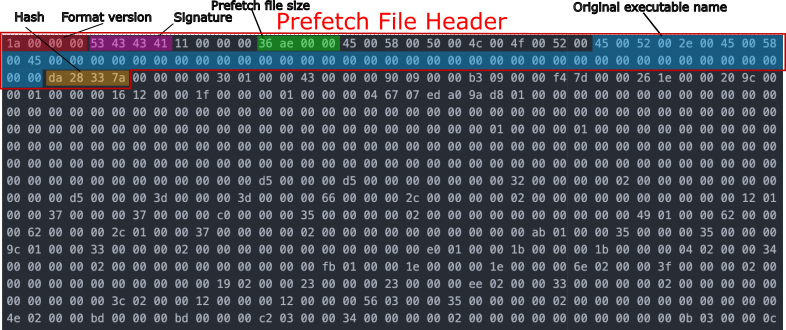
Format version: Link to heading
For the different windows versions, the prefetch format version is different:
- 17 (0x11) - Windows XP, Windows 2003
- 23 (0x17) - Windows Vista, Windows 7
- 26 (0x1a) - Windows 8.1
- 30 (0x1e) - Windows 10
Signature: Link to heading
- SCCA - Windows XP to Windows 8.1
- MAM – Windows 10/11
Original executable name and hash: Link to heading
The two information are present in the header but are also present in the prefetch filename stored on the disk (ExecutableName.EXE-Hash).pf. The hash is use to differentiate multiple execution of the same executable.
Now that we have the header information, we can extract other artifacts from the file information sections.
For each different file version, the prefetch file information are not located at the same offset. Here is the interesting information we can find about the executable:
- Section A, B, C, and D offset and entries information – Useful to locate our artifacts
- Last Execution - Latest execution time of the executable.
- Execution Counter – How many times the executable was run.
Each of those information are located at different offsets. Depending on the file version, those offsets are not the same. You can find for each version the associated offsets here
The MAM signature: Link to heading
SCCA signature indicates that the file information is stored in plain text whereas the MAM signature indicates a compressed prefetch file. MAM Signature are present in Windows 10 and 11 prefetch files only and needs to be decompressed before it can be read. The compression method used is called XPRESS Huffman which is a Microsoft compression algorithm. We’ll see later the python3 implementation of this algorithm used for the volatility3 plugin.
If you are doing forensic on a hard drive, you probably know the Windows Prefetch Parser tool by Eric Zimmermann. However, there is no tool extracting prefetch file artifacts from memory. To this end, we are now going to see the extraction and parsing of prefetch files with volatility3.
Volatility3 Prefetch plugin Link to heading
To be able to extract the prefetch file and parse them from a memory dump, we need to go through theses major steps:
- Scan for prefetch files using the “filescan” plugin;
- Dump each prefetch file in a bytearray;
- Identify each Prefetch signature and decompress it if necessary (MAM signature);
- Parse the Prefetch and extract the interesting artifacts;
- Render the result.
When developing the plugin, I had to implement the Microsoft’s XPRESS Huffman decompression algorithm in python3 to be able to read Windows 1.X prefetch files. I have used the provided Microsoft pseudo code of the algorithm available . The python3 implementation of the algorithm itself is available on the forensicxlab’s github : https://github.com/forensicxlab/Xpress_LZ77Huffman The volatility plugin is using a derived version of this algorithm, which will return the file even if the PF is incomplete so we can extract information.
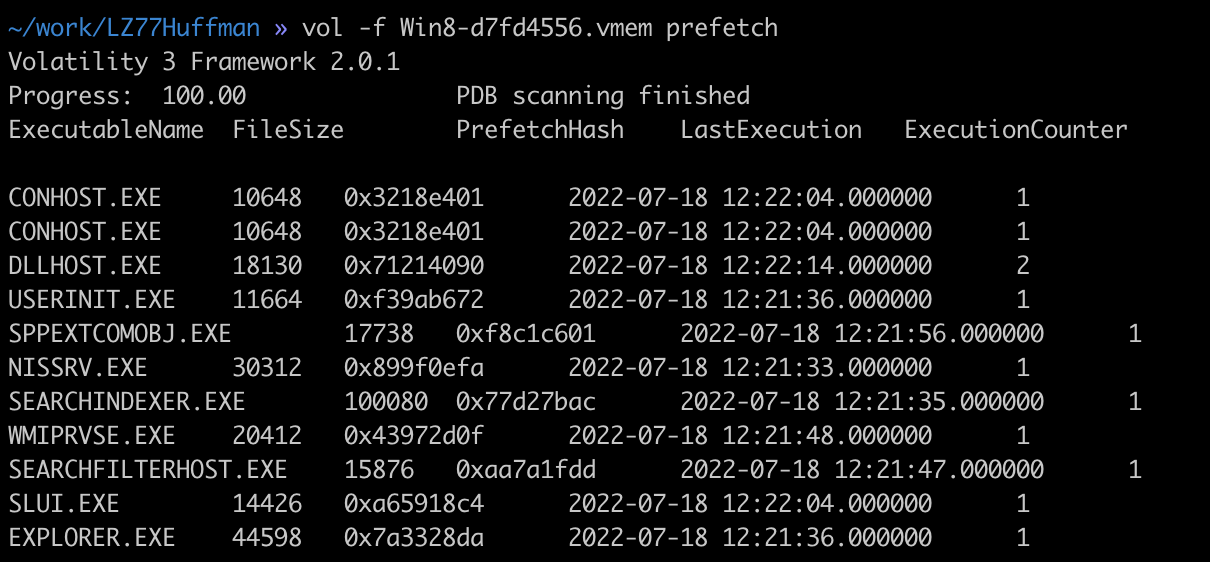
Conclusion Link to heading
The plugin was tested on Windows 7, Windows 8.1 and Windows 10 vmem memory dumps. The plugin code can be found on the forensicxlab’s github and will be submitted to the volatility3 community for a potential integration to the framework. You should Identify each steps described before in the source code comments. Do not hesitate to reach me at felix.guyard@forensicxlab.com, or to make a pull-request on the repository to enhance this plugin or this article.
Happy Hunting!