Abstract Link to heading
Video games have become an integral part of our culture, providing entertainment and social opportunities. Unfortunately, criminals have also begun to take advantage of modern video games and their ever-growing capabilities to conduct illegal activities. Organized crime, hate spread, and pedophilia have been documented occurring within games, opening up the potential to a world of cybercrime.
Digital forensics on the Steam application can be especially useful for law enforcement in tracking down and prosecuting these cybercriminals. By investigating video game applications like Steam, digital footprints that can be used to link individuals to games, transactions, and even other players. Once these links are established, they can then used to build a case against the perpetrators. In this article, the reader will learn about some artifacts that can give releavant information left on a disk during a post-mortem analysis.
Note : All of the information about the investigated user displayed in the following findings are redacted.
Steam integrated browser artifacts Link to heading
A dedicated web browser is built into the Steam software (the Steam application is just another derived version of chromium). It can even be accessed while playing in game. It is a convinient way for gamers to look for something online without quitting the game. Therefore, interesting artifacts can be retrieved in the same way a digital forensics investigator would do when performing a Chrome analysis.
Locations:
- Windows 10 :
%UserProfile%\AppData\Local\Steam\htmlcache\ - Ubuntu :
$HOME/.local/share/Steam/config/htmlcache/ - MacOS :
$HOME/Library/Application Support/Steam/config/htmlcache/
By using opensource investigation tools like Hindsight 1, one can extract browser Cookies (and decrypt them), Cache, Session Storage, Local Storage, History, Visited Links, etc…
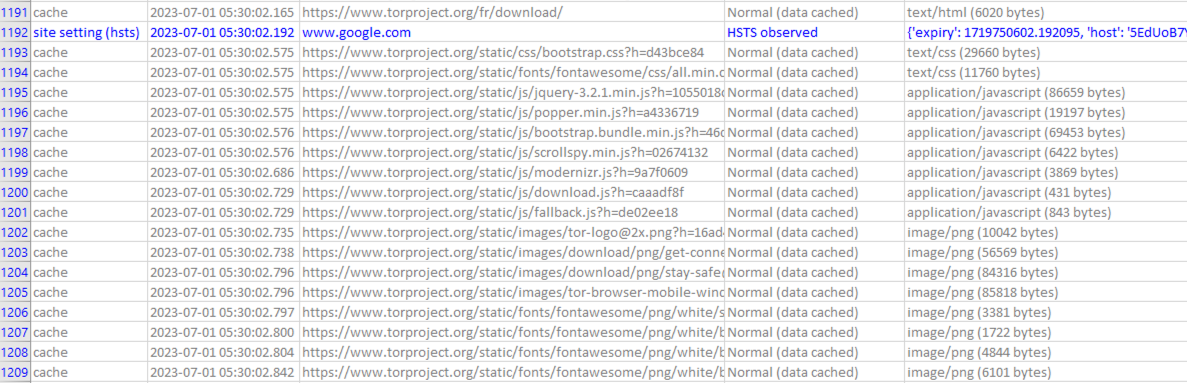
On Windows, a base64 encoded DPAPI key can be recovered in the following path :
%UserProfile%\AppData\Local\Steam\htmlcache\LocalProfs.json
DPAPI encryption is based upon user password, therefore one may be able to retrive the cleartext value of encrypted cookies. Learn more about DPAPI here : https://www.passcape.com/index.php?section=docsys&cmd=details&id=28#32
Miscellaneous: Friends, Installed games, Playtime and game sessions Link to heading
As a digital forensics investigator, you might be interested about the Steam friends of the user you are investigating, the games he played and for how long. All of the Steam users and games have unique IDs used to talk to the servers and get various information.
Steam user account information Link to heading
The user has two assigned unique IDs :
- The Steam ID : Used to identify a profile on the Steam community website.
- The account ID : Used to link the account to other various information (subscription, owned games,…)
Recovering the user’s Steam id Link to heading
Locations:
- Windows 10:
%programfiles(x86)%\Steam\config\loginusers.vdf - Ubuntu:
$HOME/.local/share/Steam/config/loginusers.vdf - MacOS:
$HOME/Library/Application Support/Steam/config/loginusers.vdf
Note : The VDF file format is the Valve’s KeyValue text file format. It is similar to the json file format.
Content:
"users"
{
"76561199524123422232"
{
"AccountName" "Jean"
"PersonaName" "superjean"
"RememberPassword" "1"
"WantsOfflineMode" "0"
"SkipOfflineModeWarning" "0"
"AllowAutoLogin" "1"
"MostRecent" "1"
"Timestamp" "1688740727"
}
}
Using the Steam ID, one can retrive more information about the community profile by browsing to https://steamcommunity.com/actions/ajaxresolveusers?steamids=[STEAM_ID].
JSON result:
[
{
"steamid":"765231213229864",
"accountid":15623422136,
"persona_name":"superjean",
"avatar_url":"0000000000000000000000000000000000000000",
"profile_url":"",
"persona_state":1,
"city":"Athabasca",
"state":"Alberta",
"country":"CA",
"real_name":"Jean Pierre",
"is_friend":false,
"friends_in_common":0
}
]
Note : there is no need to be authenticated to Steam to retrive those data.
Friends Link to heading
Locations:
- Windows 10 :
%programfiles(x86)%\Steam\userdata\[account ID]\config\localconfig.vdf - Ubuntu :
$HOME/.local/share/Steam/userdata/[account ID]/config/localconfig.vdf - MacOS :
$HOME/Library/Application Support/Steam/userdata/[account ID]/config/localconfig.vdf
The user’s friend list can be found at the begining of the file under the “friends” section.
[...]
"friends"
{
"1232434343"
{
"NameHistory"
{
"0" "superjean"
}
"avatar" "8376ba022787d9a86309b7b2b68e9994056c06e7"
"name" "superjean"
}
"PersonaName" "superjean"
"communitypreferences" "1800280130013800"
"11132322"
{
"name" "Pierre"
"NameHistory"
{
"0" "Pierre"
}
"avatar" "9f0c155db20221ade1ca5e1de4a705049f540bac"
}
[...]
}
The first ID is always the account ID of the user you are investigating (the user is friend with himself). Next, all of his friends are listed alongside with their ID.
To recover more information about the user’s friend one may use the following request :
https://steam-chat.com/miniprofile/ACCOUNT_ID/json/
This request has to be made online; it is usefull to see if the user changed his informations when performing the post-mortem analysis.
With this, the investigator will be able to confirm :
- The user’s friend name (may have changed when performing the post-mortem analysis)
- Retrive the profile picture (can be great to build a graph).
Owned and Installed games Link to heading
Inside localconf.vdf it is also indicated the games owned by the user, the last play time and how much time he spend on each game:
[...]
"Software"
{
"valve"
{
"Steam"
{
"apps"
{
"7"
{
"cloud"
{
"last_sync_state" "synchronized"
}
}
"760"
{
"cloud"
{
"quota_bytes" "20000000000"
"quota_files" "50000"
"used_bytes" "2177105"
"used_files" "12"
}
}
[...]
}
}
}
}
Making a similar request with the Steam app id, one can retrive the metadata about the installed game to make better user profiling:
Request : https://store.steampowered.com/api/libraryappdetails/?appid=[STEAM_APP_ID]&l=english
Connected device(s) Link to heading
Locations:
- Windows 10 :
%programfiles(x86)%\Steam\config\remoteclients.vdf - Ubuntu :
$HOME/.local/share/Steam/config/remoteclients.vdf - MacOS :
$HOME/Library/Application Support/Steam/config/remoteclients.vdf
The remote client cache can tell us about the hostnames and public IP adresses that were recently used to connect to Steam (via browser or desktop application). It might be possible to even guess the operating system that were used if some default naming conventions were used. In the bellow example, we can guess that the source OS is probably Windows.
"RemoteClientCache"
{
"1012008522321213291784"
{
"hostname" "DESKTOP-3QEVFIQ"
"lastupdated" "1688740718"
"lastresult" "20"
"ippublic" "193.43.70.103"
"apps"
{
}
}
"32802461232113594"
{
"hostname" "DESKTOP-BNO4NTQ"
"lastupdated" "1688740718"
"lastresult" "20"
"ippublic" "193.43.70.103"
"apps"
{
}
}
}
Application logs Link to heading
There is a lot of logs saved linked to the activity of the application. They can be usefull to obtain more context in some cases.
Locations:
- Windows 10 :
%programfiles(x86)%\Steam\logs\ - Ubuntu :
$HOME/.local/share/Steam/logs/ - MacOS :
$HOME/Library/Application Support/Steam/logs/
Example :
[...]
[2023-07-07 18:44:03] Loaded store 'machineuser' from '[...]/Library/Application Support/Steam/local.vdf' successfully
[2023-07-07 18:51:20] Flushed store 'userlocal' to '[...]/Library/Application Support/Steam/userdata/[...]/config/localconfig.vdf'
[2023-07-07 19:06:57] Flushed store 'userlocal' to '[...]/Library/Application Support/Steam/userdata/[...]/config/localconfig.vdf'
[2023-07-07 19:21:46] Flushed store 'userlocal' to '[...]/Library/Application Support/Steam/userdata/[...]/config/localconfig.vdf'
[2023-07-07 19:35:46] Flushed store 'userlocal' to '[...]/Library/Application Support/Steam/userdata/[...]/config/localconfig.vdf'
[2023-07-07 19:57:25] Flushed store 'install' to '[...]/Library/Application Support/Steam/config/config.vdf'
What about the user conversations ? Link to heading
Unfortunately the user conversations are not saved on disk but on the Steam’s servers. The channel used to send messages is encrypted through a socket using X509 certificates. You might be able to get those by collaborating with the Steam organization if you are law enforcement. It might be possible to retrieve conversations in the web browser cache or by using memory analysis though I did not dig into any of these hypotheses yet.
Conclusion Link to heading
To conclude this article, we were able to retrieve a good amount of information about the user. Those artifacts were found from my own research, there might be more interesting artifacts that were missed when preparing this blog article. If you are looking to automate your artifacts collection, a python library 2 exists to parse vdf files. Hopping it will help you when performing your investigations. Do not hesitate to reach me at felix.guyard@forensicxlab.com to enhance this article.